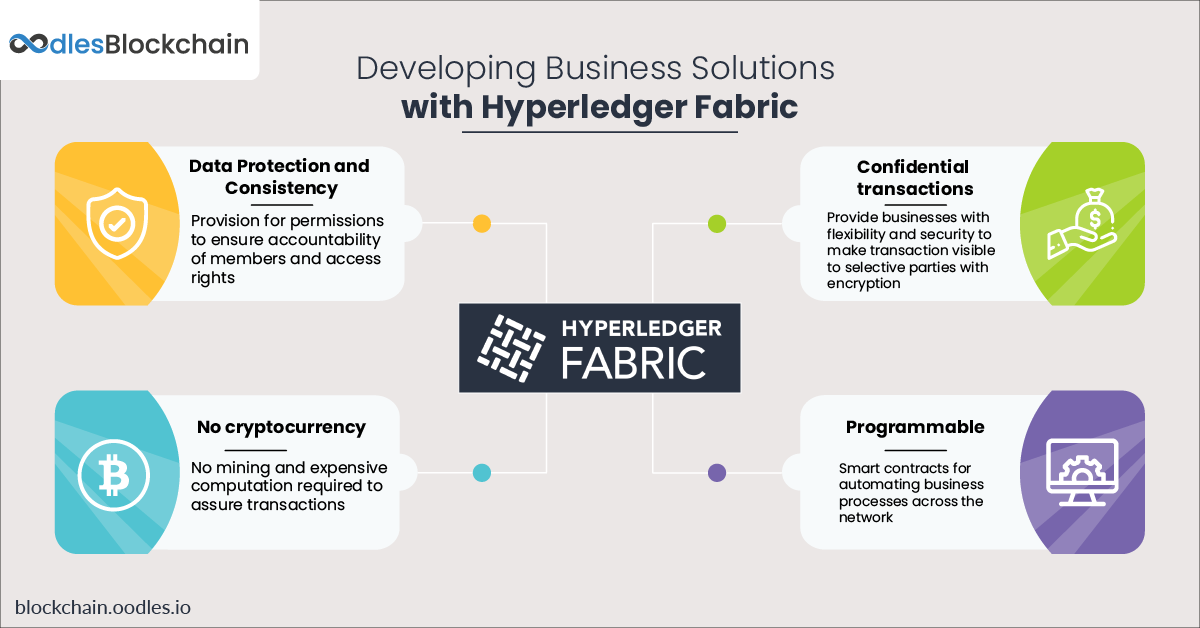
-
Hyperledger Fabric is a platform that fits best for developing private and permissioned business solutions with distributed ledgers. It enhances the confidentiality, resiliency, flexibility, and scalability of the network with its modular architecture. Hyperledger Fabric enables developers to build private blockchain solutions for organizations looking to set up private consortiums. Unlike public blockchains where anyone can join the network, users have to enroll through Membership Service Provider (MSP).
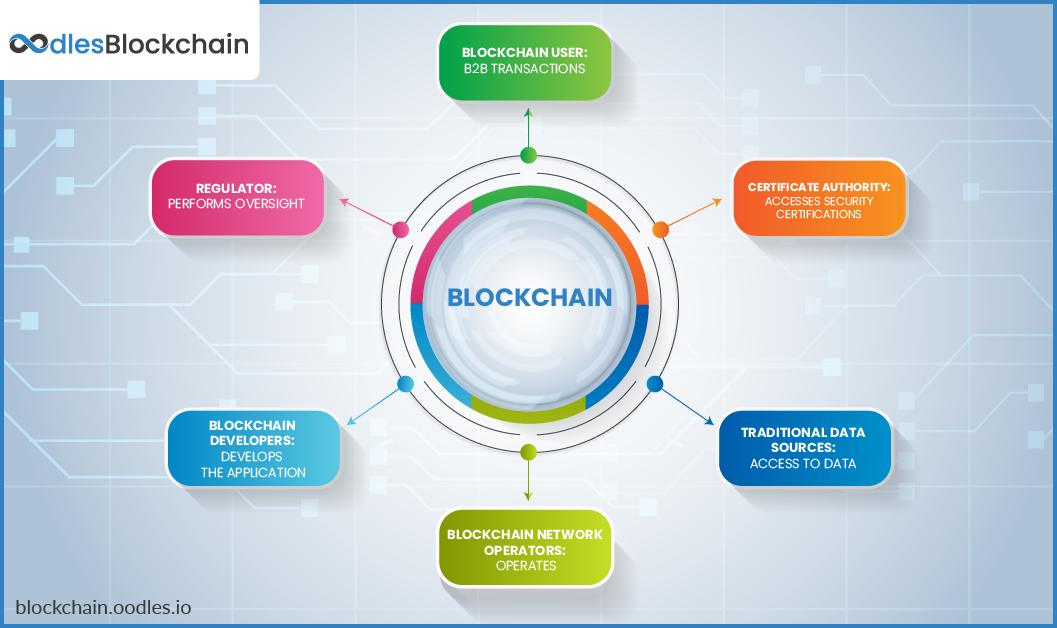
Hyperledger Fabric Network Model
Its network has features that enable the development of standard customizable enterprise blockchain systems. Assets: Facilitating monetary value exchange across the network Chaincode: Reducing the required levels of trust and verification across node types, and optimizing network performance and scalability Ledger: Encoding transactions for each channel, including SQL-like query provisions Channels: Enabling multi-lateral transactions with enhanced levels of privacy and confidentiality Security and Memberships: Authorizing and assigning regulators and auditors as members to detect and trace transactions Consensus: Enabling network operators to select a consensus method that fits best to represents participants' existing relationships in the network
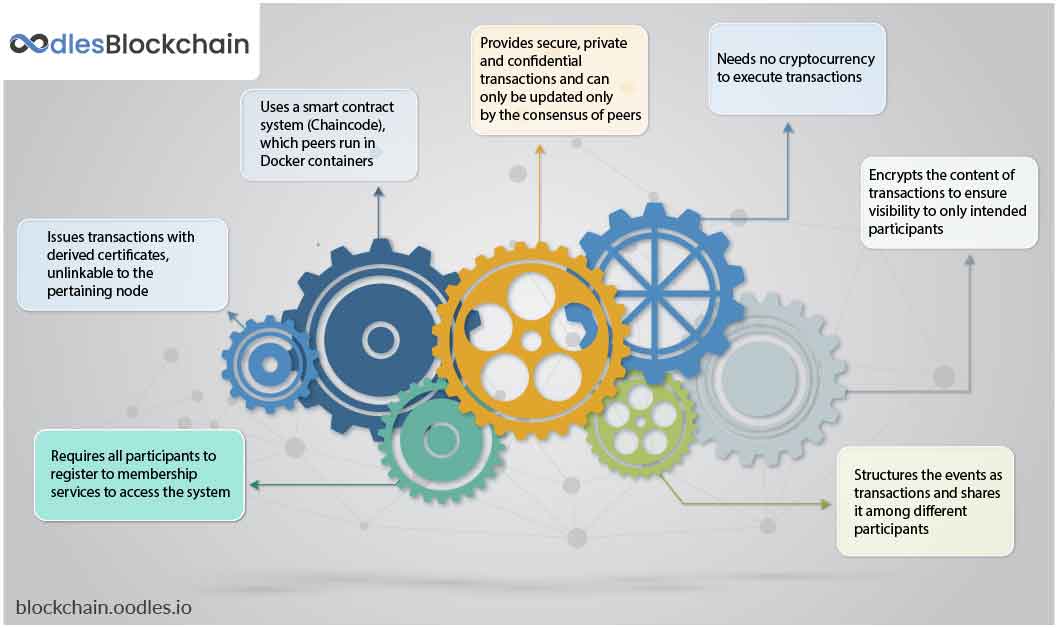
Modular Architecture for Development
- Hyperledger developers create the application and smart contract
- They deploy the application on the server and the smart contract on a peer using DEPLOY
- A verified user interacts with the app by sending orders (INVOKE) or retrieving information (Query) through the smart contract
- Smart contract executes an event subscribed by the applications
Work Model of Hyperledger Fabric
 Its design makes it a truly modular, scalable, and secure foundation for enterprise blockchain solutions. It decouples peers into two distinctive runtimes with three separate roles. Commiter peers: Commit transactions, and maintain ledger and state Endorsing peers: Receive, and grant, or deny transaction proposals of endorsements Ordering peers: Approve addition of transactional events to the database, and communicate with other two peer nodes
Its design makes it a truly modular, scalable, and secure foundation for enterprise blockchain solutions. It decouples peers into two distinctive runtimes with three separate roles. Commiter peers: Commit transactions, and maintain ledger and state Endorsing peers: Receive, and grant, or deny transaction proposals of endorsements Ordering peers: Approve addition of transactional events to the database, and communicate with other two peer nodesUse Cases of Hyperledger Fabric
B2B Contracts
Hyperledger Fabric has the provision for coding business contracts that enable trusted automation of contractual agreements between two or more parties. While information remains ‘public,' B2B contracts often require privacy control over their sensitive business information. Although confidential agreements are a critical business element, there are situations in which contracts must be discoverable by all participants.
Roles
Contract Participants: Contract other counterparties Third-party participants: Stakeholders who will guarantee the contract's integrity
Key Components
Multi-sig contract activation: When one of the counterparties execute their first contract, it goes to the pending activation state. Then, it requires signatures from other counterparties or other third party participants for activation. Multi-sig contract execution: Some contracts may also need one of many signatures to execute the contract. For instance, in financial trades, a payment instruction execution is possible when the recipient or authentic third-party confirms the shipment. Discoverability: If a business contract is seeking bids, it must be easily discoverable. Blockchain developers can use Fabric to build smart contracts that have built-in intelligence to evaluate, choose, and honor bids. Contract execution or atomicity: Atomicity of a contract guarantees that asset transfer will only occur when the recipient has received the payment. If any execution process stops fails, it will roll back the entire transaction. Contracts to chain-code communication: Contracts must communicate with chain-codes, deployed on the same ledger. Reusable contracts: Standardize the most used contracts for reuse. Auditable contract agreements: Provides provisions to third parties for auditing any contract. Contract life-cycle management: Enables an efficient contract management system to scale the ledger network as some contacts might not be standardized. Validation access: Only nodes that have validation rights can verify and validate transactions of B2B contracts. View access: Only accounts with predefined access rights can view and interrogate the B2B contracts as they often include sensitive information.
Manufacturing Supply Chain
Final assemblers, like automobile manufacturers, can form a supply chain network managed by peers and suppliers. It facilitates better management of suppliers and makes them more responsive to various events, such as vehicle recall events. The network protocol must enable supply chain participants to input and track numbered parts produced and used for a specific vehicle. Also, it should have the backward searchability for provenance tracking of goods, which may include other suppliers.
Roles
Final assemblers: Entities that assemble the final product. Parts Suppliers: Supplier of parts. They can also be assemblers, by assembling parts received from other sub-suppliers, and then sending the product to the final assembler.
Key Components
Payment upon the delivery of goods: Upon receiving of parts, it will require integration with off-chain payment systems to execute payment instruction. Third-party Audit: The solution must allow all supplied parts to be auditable by third- parties. For instance, regulators may require tracking of the total numbers of supplied parts by a specific supplier for tax accounting. Shipment obfuscation: It requires balance obfuscation to restrict suppliers from deducing activities of other suppliers. Market size obfuscation: It obfuscates overall balances to restrict part suppliers from deducing their own market share for negotiating contractual terms. Validation access: Only nodes with validation access will have the right to validate transactions, such as the shipment of parts. View access: Only accounts that have view access will have the right to interrogate the balance of the shipped and available parts. Related Reads
Use cases for additional requirement and scenarios
Single Trade, Single Contract
From the capture of a trade by the front office to its final settlement, the solution will create only one contract. The intermediaries will receive the same electronic contract. Later, counterparties will also use it to validate the trade. Eventually, the securities depository will execute the trading instructions mentioned for settling it. However, in bulk trades, there will be divided sub-contracts that are always linked to the parent contract.
Interoperable Assets
If a company needs 10,000 units of asset B but owns only 5,000 units of asset B, a solution for exchanging assets is essential. Although the existing market may not provide sufficient liquid options to achieve this trade, liquidity between asset A and C will be available. So, instead of market limit settlements on direct trading (A for B), the network chain will connect buyers with buried sellers, determine the best pair, and execute the transaction.
Concluding Thoughts
Verifiable identities of the participants is a primary requirement for private industrial networks. Hyperledger Fabric is best suited for ensuring the identity of participants and the privacy of specific transactions on the network. Fabric provides a modular architecture with permission-based membership services, which require all network participants to have verified identities to access transaction information. It has implications in industries like healthcare and real estate, as they are bound by the data protection regulations. They mandate these industries to maintain data about various participants and their permissions to access various data points. Fabric provides such permissioned-based membership. Only the permissioned participants get access to the necessary details. Such a data partitioning system developed on the blockchain enables specific data points to be accessible to only the parties that require it. Its modular architecture acts as a foundation for blockchain-based products and applications development with plug-and-play components for private enterprise ecosystems. Oodles is a Hyperledger development company that has expertise in enabling businesses and startups to streamline their processes with transparent and efficient transactions. Our blockchain team evaluates intricate details of the solutions and use multiple benefits of Hyperledger to fulfill your business requirements. If you're looking for efficient and effective Hyperledger application development services, connect with our consultants and tech experts.

Our Offices
INDIA
Emaar Digital Greens, Sector 61,
Gurugram, Haryana
122011.
Welldone Tech Park,
Sector 48, Sohna road,
Gurugram, Haryana
122018.